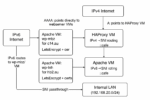
This is a structured visual and text-based overview of my IPv4 + IPv6 dual-stack web architecture with HAProxy and self-contained certs.
🌐 Final Architecture Diagram (Text-based)
┌──────────────────────┐ ┌──────────────────────┐
│ IPv6 Internet │ │ IPv4 Internet │
│ (native routing) │ │ (single IP NAT) │
└────────────┬─────────┘ └──────────┬───────────┘
│ |
│ AAAA: points directly | A: points to
│ to webserver VMs | HAProxy VM
▼ ▼
┌─────────────────────┐ ┌──────────────────────┐
│ Apache VM: wp-mbz │ ◀────────────── │ HAProxy VM │
│ ── for c14.au │ SNI │ IPv4 → SNI routing │
│ IPv6: ::cafe:babe │ passthrough │ IPv6: ::cafe │
│ LetsEncrypt + certs │ │ routes to wp-mbz/hb2 │
└─────────────────────┘ └──────────┬───────────┘
│
┌─────────────────────┐ ▼
│ Apache VM: wp-lnh │ Internal LAN
│ ── for hb2.au │ (192.168.16.0/20)
│ IPv6: ::cafe:d00d │
│ LetsEncrypt + certs │
└─────────────────────┘
📄 Structured Description
🧩 Components
| Role | Name | Addressing |
|---|
| Reverse Proxy | haproxy | IPv4: 192.168.20.17, IPv6: ::cafe |
| Webserver #1 | wp-lnh | IPv4: 192.168.20.47, IPv6: ::cafe:babe |
| Webserver #2 | wp-mbz | IPv4: 192.168.20.49, IPv6: ::cafe:d00d |
🌐 DNS Setup
| Record Type | Domain | Points To |
|---|
| A | c14.au | public IPv4 → NAT → HAProxy |
| AAAA | c14.au | ::cafe:d00d |
| A | hb2.au | public IPv4 → NAT → HAProxy |
| AAAA | hb2.au | ::cafe:babe |
🔐 SSL Certificates
- Each webserver (
wp-mbz, wp-lnh) runs dehydrated to obtain and renew its own Let’s Encrypt cert
- Certs are:
- Served directly over IPv6
- Accessed via HAProxy over IPv4 (SSL passthrough, not terminated)
- No certs installed on HAProxy VM
🔁 Traffic Flow Summary
| Protocol | Path | Cert Presented | SSL Terminated |
|---|
| IPv6 | Client → ::cafe:d00d | wp-mbz | At Apache |
| IPv6 | Client → ::cafe:babe | wp-lnh | At Apache |
| IPv4 | Client → NAT → haproxy | Routed by SNI | At Apache |
| VPN IPv4 | Client → 192.168.20.17 | Routed by SNI | At Apache |
🔧 VPN & Internal Access Notes
- Split DNS via
dnsmasq resolves c14.au and hb2.au to 192.168.20.17 for VPN clients
- Firewall/NAT rules in OPNsense were adjusted:
- NAT reflection was blocked due to rule order
- Custom firewall rule now allows VPN-to-HAProxy traffic
🔒 Security Score
- Verified with SSL Labs:
- ✅ A+ for both IPv4 and IPv6
- ✅ No mismatched certs
- ✅ TLS 1.3 and strong ciphers in use
✅ Status
🏁 Final setup is clean, self-renewing, dual-stacked, and robust.
ChatGPT: “You’ve built something most small hosting setups never reach!”