Navigating the Digital Landscape.
All information presented here is available online.
Visit https://c14.au/2025/08/id-3209/understanding-the-online-world/
Table of Contents (TOC)
1. Safety Apps (Emergency Plus)
2. Scams: Phishing & Fake QR Codes
4. Recognising The Domain — Why It Matters
5. What is hiding in QR-Codes?
7. Tracking, Fingerprinting & Data Brokers
10. Digital Payments & NFC Security
11. PayPal, Google Pay, Apple Pay
12. Passwords, Managers & Digital Legacy
1. Safety Apps

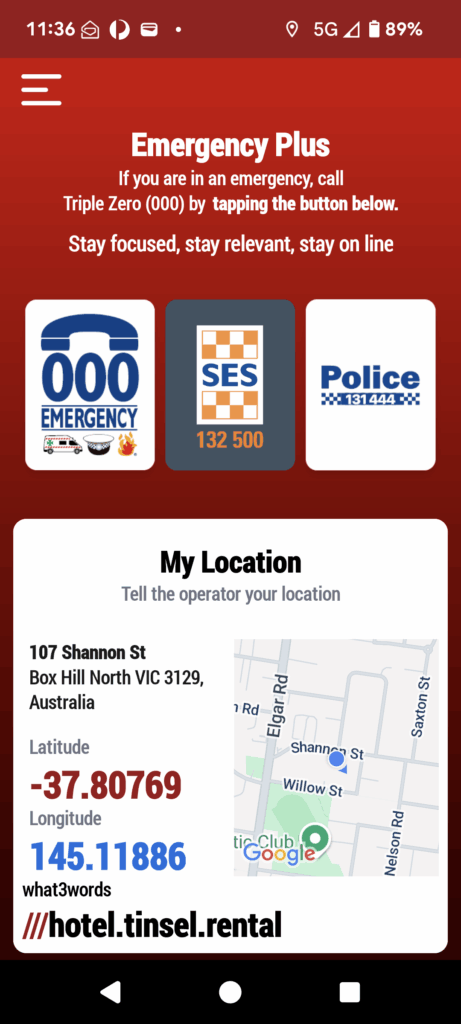
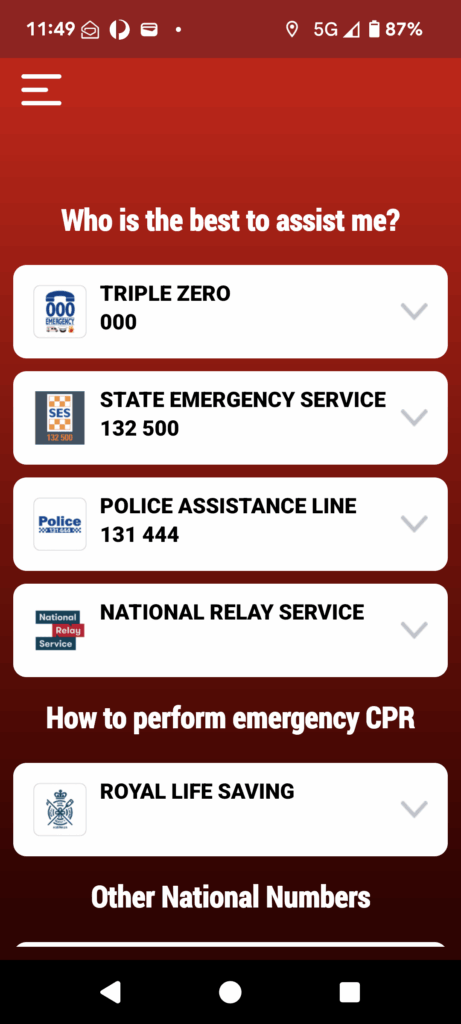
Emergency Plus App – Your Lifeline in Australia
- What is it? A free government-backed smartphone app for all Australians.
- Purpose: To help you call the right number for emergency and non-emergency situations.
- Key Functionality: It’s effectively a “smart” speed-dialer. With a single tap, you can connect to:
- Triple Zero (000) for police, fire, or ambulance emergencies.
- State Emergency Service (SES) for storm and flood help.
- Police Assistance Line for non-urgent matters.
- Ownership: The app is a government initiative, owned by the Commonwealth of Australia.

Why it’s so useful & The Power of Location
Pinpoint Accuracy: The app uses your phone’s GPS to find your precise location, even in unfamiliar or remote areas.
Crucial Information: It displays your location in three easy-to-read formats:
- Street address
- Latitude and Longitude (GPS coordinates)
- A unique, simple what3words address
Faster Response: Providing these exact details to the call-taker helps emergency services get to you faster, which can be critical in a life-threatening situation.
Offline Capability: The what3words feature works even without mobile data, so you can still give your location in areas with no internet connection. Also works over CB radio if there is no phone coverage.
2. Scams: Phishing & Fake QR Codes
Does this look legitimate to You?
And what about this one:
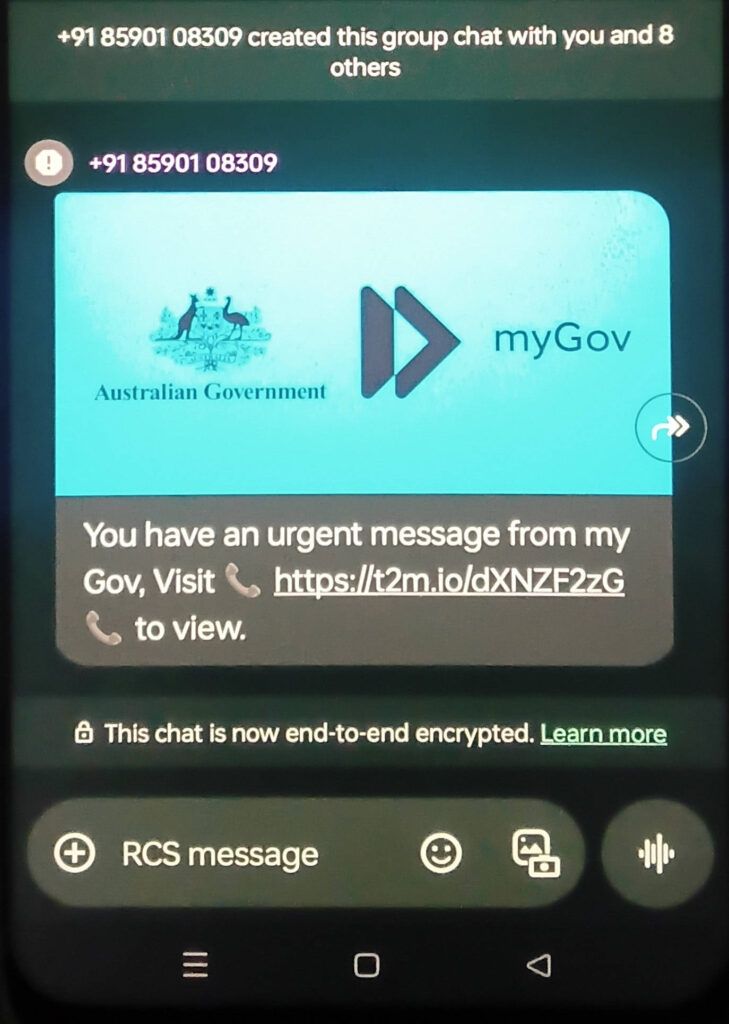
We will examine this in more detail but first we need to lay some ground work.
3. How Data Travels
The Two Things HTTPS Does
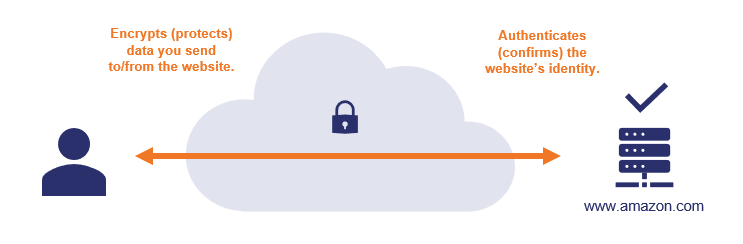
When you go to a website that starts with https://, that tells you two very specific things:
- A third party has authenticated the website. The website has been authenticated to verify it is the website it claims to be — if your browser bar says https://www.amazon.com, you can be confident that you’re actually on amazon.com.
- The site uses encryption. Data you send to/from the website is encrypted so other parties can’t see/steal it—you can submit credit card numbers or other sensitive data and know that nobody can intercept your info while it’s making the trip to amazon.com.
What HTTPS Does Not Do
It knows nothing about the legitimacy of the domain owner, operational and legal compliance.
It offers no protection regarding:
- How the website processes, stores, or uses your data once received
- Whether the site shares your information with third parties
- The security of the server’s database or backend systems
- Data retention policies or deletion practices
- Cross-site tracking or behavioral profiling
Your encrypted credit card number arrives safely, but HTTPS doesn’t govern what happens to it afterward.
HTTPS is an essential foundation for web security, but it’s just one piece of a much larger security and trust puzzle. Users must still exercise critical thinking, verify site legitimacy through other means, and remain vigilant about the information they share online.
4. Recognising The Domain — Why It Matters:
Even with HTTPS, you must be able to recognise the real domain name — not just glance at the address bar.
Scammers often try to fool you by:
- Using misleading subdomains (e.g.
https://commbank.login.verify-now.com/) - Using misleading paths (e.g.
https://money-plan.se/auth/commbank/login/) - Using lookalike domains e.g.:
paypal.sec-auth.com/secure-paypal.co/
✅ What you should look for:
- The registered domain + top-level domain (TLD) — that’s the real identity of the website.
- In
https://www.paypal.com.au/account, the domain is: paypal.com.au - In
https://secure.anz.money365.com.au, the domain is:money365.com.au - In
https://money-plan.to/commbank/secure/login, the domain is: money-plan.to
- In
🔎 Tip: The real domain is usually made of two or three parts, ending just before the first single
/after the TLD (e.g..com,.org,.com.au, .co.uk,.se, .ai, .to, .de).
The rest — subdomains and paths — can be crafted to look convincing but mean nothing about who owns the site.
❌ Don’t be fooled by:
- Anything that appears before the domain (e.g.
commbank.orsecure.) - Anything that appears after the domain (e.g.
/NAB/login/verify) - The presence of a padlock icon — scammers can use HTTPS too.
🧠 Your job as the user:
- Focus on the full domain name, including the TLD.
- Ignore everything after the first single slash (the path) — it can say anything.
- Use your judgement — if something feels off, don’t enter personal info.
Identifying the Domain
Consider this URL:

Your job is to learn the important components of a URL so that you can identify the domain.
The important components of a URL are marked here:
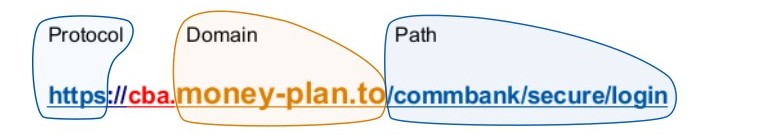
Protocol: Usually https (HyperText Transport Protocol Secure). Older, insecure sites may still use http – you can visit the site but any information you enter is not secure – it can be intercepted.
Domain: Look for the first single slash / The domain parts are left of it separated by dots: .
Only the right-most 2 or 3 elements count towards the domain. Further to the left are sub-domains which are unimportant. A common sub-domain is “www“. In the URL here it is “cba“.
Path: This is akin to a file path on a Windows PC where you might have
C:\Users\Elisabeth\Documents
and you could create folders named:
C:\commbank\secure\login
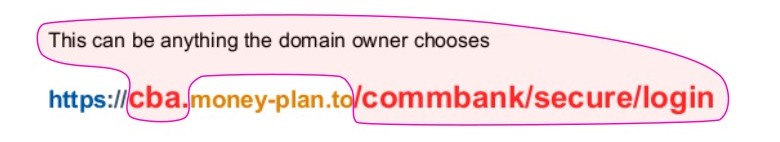
Key takeaway: the sub-domain and the path are legitimately used to organise a website into sections, subsections and pages but scammers often misuse it for deception.
We are now equipped to evaluate the messages shown earlier
When we hover on the button the browser or email client will show us the URL. Often it is displayed at the bottom left but this can vary.
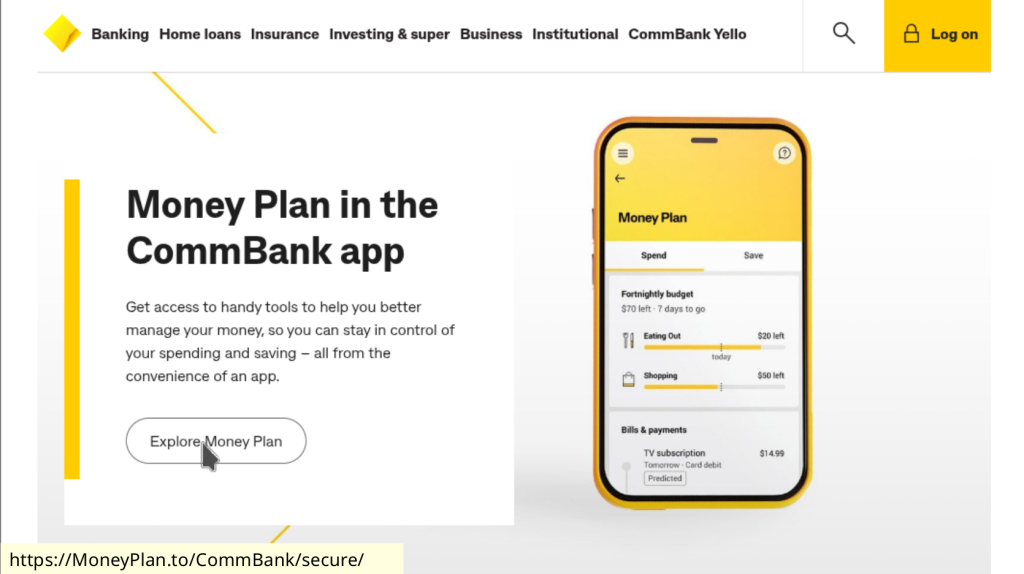
We can now identify the domain as MoneyPlan.to and because the protocol used by that domain is https we can be confident that we will be connected to the genuine domain MoneyPlan.to
Searching for the .to top level domain, we can see that .to is assigned to the Kingdom of Tonga.
The next one, and SMS message, is even easier to identify:

The phone mumber starts with a country code of 91 (India). Australia’s code is 61.
Because of https, we can also be confident that the link will connect us to the genuine t2m.io domain registered in the British Indian Ocean Territory.
Find out more
Ideally, and with some practice, you will become skillful at spotting suspicious URLs by yourself.
Occasionally, it might be less clearcut and you can check a domain’s rating at https://www.scamadviser.com/
5. What is hiding in QR-Codes?
- Machine-readable squares that encode text, often a URL
- Can link to websites, Wi-Fi settings, payment requests, or contact info
- You can’t tell what it encodes just by looking
- Use your phone’s preview or a QR-code scanner app to view before opening
- Always check the domain in a URL before clicking
- Malicious codes can lead to phishing sites, malware, or fake login pages
- Be cautious with QR-codes in public places — they may be tampered with
- If in doubt: don’t scan, or scan but don’t click
How to scan a QR-Code safely
Use a QR‑scanner app that displays the full URL or at least the host/domain, so you can verify before opening.

Trend Micro’s QR Scanner (“Safe QR Code Reader”) clearly previews the domain and performs safety checks—blocking known malicious links before you click. It’s ad‑free and free to use on Android and iOS helpcenter.trendmicro.com+10Trend Micro News+10Google Play+10.
Trend Micro is lightweight, reliable, and better at revealing full URLs than many others—many scanners only show the leading 8–10 characters Trend Micro News+15qrcodeveloper.com+15QR Code Press+15.
If on iPhone, the built‑in Camera app preview displays the host/domain, which helps catch suspicious redirects (though not always the full path) qrplanet.com.
Avoid generic QR apps that truncate URLs or display only brief previews—you need to see at least the full domain.
Always inspect the domain: misspellings, unusual country‑code TLDs, or odd-looking hosts are red flags.
If possible, scan with the app and view the full URL, then copy and paste into a browser to inspect manually before visiting.
Test your QR-Code and URL skills on this QR-Code:

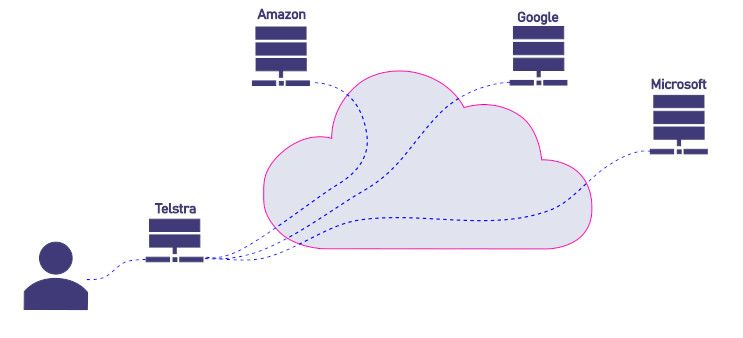
6. VPNs: Uses & Limits
What HTTPS already does (without a VPN):
- Encrypts content between your browser and the destination site.
- Prevents eavesdroppers (like others on public Wi-Fi or your ISP) from seeing:
- What you send or receive
- The specific pages you visit (e.g.
/account/login)
- But does not hide:
- The domain name you’re visiting (
amazon.com) - The fact that you’re communicating with
amazon.com, even if the content is encrypted.
- The domain name you’re visiting (
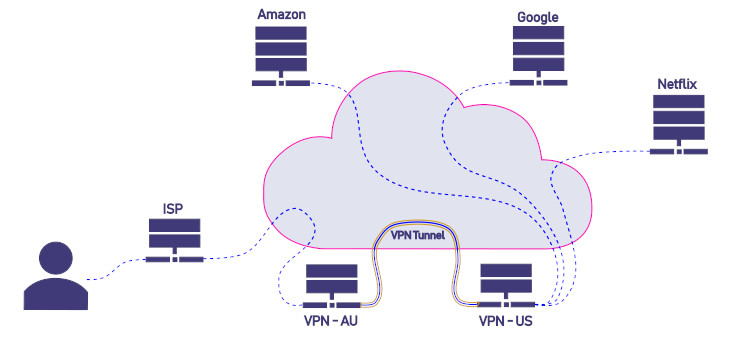
What a VPN adds (on top of HTTPS):
✅ Benefits:
- Hides destination domains from local observers (e.g. ISP, café Wi-Fi):
- Instead of seeing you contact
facebook.com, they see only that you’re connected to the VPN server. - This hides DNS requests too, if the VPN tunnels them.
- Instead of seeing you contact
- Protects unencrypted traffic (non-HTTPS), if any.
- Rare now, but still relevant for some legacy sites or apps.
- Unifies and encrypts all traffic through one secure tunnel:
- Prevents local attackers from even seeing what services you’re using.
- Helpful in hostile environments (e.g. shared networks, oppressive regimes, insecure hotspots).
❗ Limitations:
- The VPN provider sees everything your ISP would have — domains, and possibly unencrypted content.
- It does not add any extra encryption to HTTPS traffic — that part is already end-to-end between your browser and the target website.
- Does not protect against phishing, malware, or fake websites.
Visualisation
7. Tracking, Fingerprinting & Data Brokers
What is Tracking?
- Websites and advertisers track you using:
- Cookies (esp. 3rd-party)
- Embedded scripts (trackers, ads, social buttons)
- Browser storage & pixels
What is Fingerprinting?
- Identifying a user’s browser without cookies, using:
- Browser type, fonts, plugins
- Screen size, time zone, language
- System details → creates a unique profile
Why it matters
- Tracks you across sites even when logged out
- Can’t be easily cleared like cookies
- Used for profiling, targeted ads, and surveillance
How to reduce tracking
- Use privacy-focused browsers (Opera, Brave)
- Enable Tracker Blocking (on Chrome add Privacy Badger)
- Use Private Mode or, with some browsers, containers.
Fingerprinting defenses
- Minimize browser uniqueness (avoid rare fonts/extensions).
- Use Brave Browser (strong protection, randomizes fingerprint).
- Use Tor Browser (strongest defense, but overkill for most).
Who are Data Brokers?
- Buy/sell your data from apps, loyalty cards, trackers
- You have little control or visibility
- Tools like DeleteMe, SimpleOptOut help reduce exposure but cannot offer full protection.
Check how unique your browser is:
Electronic Frontier Foundation: Cover Your Tracks.
Am I unique: amiunique.org/fingerprint
8. People are the Weak Link
Most cyber breaches succeed not because of weak software — but because of tricked users.
- ✅ ~90% of cyberattacks involve human error or social engineering (source: UK NCSC, Verizon DBIR).
- ✅ Even a secure, up-to-date system can be breached if the user:
- Clicks a fake link
- Reuses a password
- Installs something dangerous
- Scans a rogue QR code
🎭 What is Social Engineering?
The art of manipulating people into giving up access, information, or control — often without them realizing it.
- It plays on trust, fear, curiosity, greed, urgency, helpfulness.
- It’s not a “hack” of your computer — it’s a hack of your behavior and your emotions.
Examples of Social Engineering in the Wild
🧲 Example 1: Curiosity Trap
You find a USB stick near your car labelled “Bitcoin account backup”.
💥 If you plug it in, it could auto-run or trick you into running malware and steal your data.
👦 Example 2: Family Bypass
Your grandkids visit and plug in a USB stick:
“It’s a cool game Benny gave me at school!”
💥 Kids aren’t malicious — but malware spreads like playground gossip.
🅿️ Example 3: Sticker Switch
Your local parking meter has a new QR code sticker for payments.
💥 Scanning it takes you to a fake site that steals card info.
🧠 Takeaway
- Be curious — but cautious
- Ask: “Who’s behind this?”, “Does this make sense?”
- Your habits, not your antivirus, are your first line of defense.
9. Windows 10 End of Support (Oct. 2025)
After this, it won’t receive security updates. You can still use it, but vulnerabilities will remain unpatched.
Implication: For banking or important accounts, it’s safer to upgrade to Windows 11.
You can also use your up-to-date smartphone or other device for your important accounts.
If Microsoft says your PC does not fulfill the minimum requirements for Windows 11 you still have options:
- Accumulate points in the Microsoft eco-system or use $ to pay for one more year of Windows 10 security updates.
- Ask a trustworthy, advanced user to use popular work-around tricks to install Windows 11 anyway.
- Some advanced users might switch to an alternative (e.g. Linux Mint).
Scare level: Low, if your software habits are cautious. But don’t ignore the date.
Digital Payments & NFC Security
Smartphone based, digital wallets have advantages over plastic cards:
- Tokenization: Instead of sending your actual card number, digital wallets use a unique, one-time token for each transaction, making intercepted data useless to fraudsters.
- Biometric Authentication: Payments are authorized with your fingerprint, face, or a PIN, ensuring that only you can use your device for transactions, even if it’s lost or stolen.
- Short-Range Communication: NFC’s extremely short range (just a few centimeters) makes it difficult for criminals to intercept your payment information from a distance.
- Secure Elements: Sensitive payment data is stored in a dedicated, isolated hardware chip on your phone, providing an extra layer of protection from malware and hackers.
A disadvantage is that this won’t work when your phone’s battery is flat.
PayPal, Google Pay, Apple Pay
Online Payment Services can provide additional security against fraudulent transactions:
- Privacy: Card details are never shared with merchants — reducing the risk of theft or misuse.
- Buyer Protection: PayPal offers refunds for items not received or misrepresented.
- Disputes: can be raised easily; Google/Apple Pay rely on your bank’s protection.
- Convenience: Store multiple cards/accounts in one place. Quick, secure checkout without retyping details.
- Enhanced Security: Uses biometrics (Face ID, fingerprint) and tokenization — real card numbers aren’t sent.
- Merchant Trust: Accepting PayPal signals credibility — accounts are verified, and bad actors risk bans or chargebacks.
Passwords, Managers & Digital Legacy
🧠 Smart password habits:
- Length matters most — aim for 12+ characters
- A few passwords? Writing them down is fine — if stored securely (e.g. locked drawer)
- For many passwords, a Password Manager is safer and easier
🛠️ Why use a Password Manager:
- Stores all your logins securely
- Creates strong, unique passwords for each site
- Family plans let you share access safely
- Recommended by the 🇦🇺 Australian Cyber Security Centre
🔑 The master password is the one you must remember — guard it well!
✅ Tips:
- Bitwarden is a good, free place to start.
- Use 2FA/MFA (Two-Factor or Multi-Factor Authentication) wherever possible.
- Keep a few critical passwords (e.g. email, bank, master password) accessible outside the manager.
